Articles
Leveraging Academia to Improve NGO Driven Intelligence
ABSTRACT
Criminals and irregular fighters target non-governmental organizations (NGOs) for a variety of political and economic reasons forcing some NGOs to increase their safety through NGO-driven intelligence. The analytic capability of NGO intelligence must be strengthened if NGOs are to survive in an increasingly dangerous operational environment. Academia, through remote access analysis, provides a non-intrusive approach to support NGO-driven intelligence.
INTRODUCTION
1 Currently, militaries effectively leverage academic institutions and resources to build theory and examine military-related topics; an appropriate example would be the work of the Gregg Centre for the Study of War and Society at the University of New Brunswick. However, academia can provide more than just theory. Practical experience in quantitative and qualitative analysis can be used to examine failed states and human security and to improve the effectiveness of non-governmental organization (NGO)-driven intelligence. The analytic capability of NGO intelligence and safety must be strengthened if NGOs are to survive in an increasingly dangerous operational environment; academia provides a non-intrusive approach to improve analysis using remote-access analysis.
2 In 2006, an estimated 800 international and indigenous NGOs1 were operating in Afghanistan; the true number is not known.2 Many of these NGOs currently operate independently and are unable or unwilling to access government intelligence or information resources that may improve their security. This article addresses independent NGO insecurity from an intelligence point of view and demonstrates the potential of improving NGO-driven intelligence by leveraging academia as a means to improve NGO analytic capability. The security of NGOs should be of interest to personnel operating in or studying Afghanistan because security and development are entwined.3
3 To begin, the article loosely maps out the threat to NGOs, including the political and financial power of aid, the understanding of aid by criminals and insurgents,4 and the political and cultural threat that NGOs pose to insurgents. Next, a case study of NGO security incidents in Afghanistan (2005-06) demonstrates the potential for NGO-driven intelligence. The source data is tacit, latent, open-source5 information gleaned from NGO-generated security incident6 reports. Blending traditional intelligence with social science research methods creates an intelligence product that is uncomplicated and does not intrude on NGOs’ operations or security. Due to the nature of their role, NGOs have a plethora of information at their disposal but lack significant analytic capability and are reluctant to share detailed information for analysis with militaries or governments.7 The article concludes with a recommendation for closer relationships between NGOs and academia as a means to increase NGO analytic capacity and quality of intelligence products. Despite NGOs’ significant capability to increase governmental capacity and legitimacy, research into NGO security is in its infancy.
4 Academics have yet to provide one overarching definition of intelligence because of the variety of activities and actors it encompasses.8 In this article, NGO-driven intelligence is defined as the collection, collation, analysis, and dissemination of processed tacit, latent, and open-source information designed to provide NGOs with situational awareness and an understanding of the threat environment.
5 The focus of NGO-driven intelligence is the generation of material that facilitates survival of the NGO and its mandate. The purpose of NGO-driven intelligence is to make intelligence available to NGO decision-makers, providing them with the opportunity to mitigate risk to national and international personnel, material, and equipment. The words, intelligence and even security are rarely used within NGO or UN literature because of their negative connotations.9 “Safety” is the word most commonly used to describe NGO intelligence efforts. Before discussing the improvement of NGO security, it is necessary to establish the risk to NGOs.
The Risk to NGOs
6 Research into NGO security is in its infancy and little academic research exists regarding NGO-driven intelligence or security products.10 The lack of data on NGO security has forced researchers and NGOs alike to rely on impressions and anecdotal evidence to drive their operational security policies.11 The widespread perceptions of mounting threats to NGO workers have driven many organizations to formalize, reform, and seriously reconsider their responsibility for both national and international workers.12
7 What research that does exist indicates NGOs operating in hostile environments are at greater risk than ever. Between 2002 and 2006, there was a 400 percent increase in insurgent security incidents against NGOs.13 RAND reported that the lethality of the security incidents (incidents causing deaths) has increased 800 percent during the same reporting period.14 Violence directed at NGOs in Afghanistan has increased as the insurgency grows and has reduced NGO freedom of movement.15
8 The nature of NGOs’ work no longer protects them.16 Past security methods, including acceptance practices, may no longer be as effective because the nature of warfare has evolved. David Kilcullen has argued that insurgency is a likely vehicle future opponents can use to bypass conventional military and political power.17 Frank Hoffman has argued that, in this period of extremism, there will be a blurring of war, peace, combatants, and non-combatants in perpetual hybrid war.18 Other participant observers go so far as to assert that humanity is under assault. Even if one disagrees with Hoffman or other analysts, obviously violent conflict has become unrestrained and is comprised of a complex mixture of networked criminality, corruption, religious fundamentalism, ethnic and communal violence, forced mass migration, illegal resource exploitation, and violent competition for life-sustaining resources, such as land and water.19 Non-state violent actors within the conflict will likely be adept at exploiting their environment; proficient in the use of increasingly portable firepower; use enabled electronic communications and be well informed; and effectively combine media, culture, and nationalism to shape the information environment to their benefit. Within unrestrained violent conflict, interconnected threats, such as crime used as a means to fund insurgent efforts, are common. Despite being at risk, NGOs will likely continue to play a prominent role in stability operations.
9 The instability created by a constantly changing threat environment in Afghanistan contributes to NGO insecurity and undermines reconstruction efforts. Threats and security incidents impede the ability of NGOs to access beneficiaries, deliver humanitarian aid, and implement urgently needed reconstruction and development projects.20 For example, during the time period of 22 July-22 August 2009, the Ministry of Rural Rehabilitation and Development’s National Solidarity Programme reported that increased security risks caused the suspension of activities in 1,340 communities in 15 provinces in Afghanistan.21 Effective NGO intelligence assessments may have reduced the number of failed programs by indicating the vulnerability of the security environment, meaning time and resources may have been preserved.
10 NGOs are attacked because they are brokers of valuable commodities in a conflict zone. NGOs operate in an environment that is so complex that Mark Duffield has described it as neo-medieval.22 Within this confused and complex security environment, NGOs are attacked because they provide valuable goods and services, offer some stability, are perceived as providing aid to the government, and are usually culturally different from the population. Whether they realize it or not, NGOs are high-value targets because they are power brokers in the greater security, political, social, and economic landscape.
11 In any insurgency, the people are the prize; therefore, in an insurgent war control over the material that keeps the populace alive means victory.23 NGO power originates from a seemingly limitless supply of humanitarian aid.24 Thus perceived as wealthy, international NGOs are prime targets for theft and extortion by opportunistic individuals or organized crime.25 Consisting of locally valuable commodities, humanitarian aid provides a tempting target to any aggressor, whether criminal or insurgent. It also represents considerable political power. Stolen humanitarian aid can sustain the aggressor; selling the aid becomes a source of income, trade, or means of obtaining weapons; and distributing the aid provides a means to coerce the population, enhancing the aggressor’s political power.
12 To have legitimacy, the Afghan government must have resources for reconstruction, economic development, and infrastructure. The bulk of those resources are administered by foreign NGOs. However, over the centuries, foreigners have repeatedly invaded Afghanistan. Such a history has built resentment toward foreign interference within Pashtu tribes within their state.26 In the eyes of some Afghans, NGOs are morally corrupt and part of a foreign intervention in Afghan affairs.27 The very legitimacy and stability NGOs are attempting to create may be threatened unless resources and development efforts have a palatable Afghan “face” and moral/cultural position.
13 Insurgents, warlords, and criminals may perceive NGOs not just as government supporters but also as representatives of imperialism, neo-colonialism, or at least an alien political agenda. NGOs active with Provincial Reconstruction Teams (PRTs) are associated with intelligence collection. Sippi Azarbaijani-Moghaddam et al. have noted that “Many . . . felt that the Taliban and their spies were suspicious of people who were in regular contact with PRTs.”28 Since many NGOs are based in government administrative centers, NGOs are guilty of collaboration by association.29 Moreover, NGOs serve as a basis for stability by providing the essentials of life while enhancing Afghanistan’s infrastructure. This spreads the government’s authority and legitimacy, eroding the chaos in which insurgents, warlords, and criminals thrive.
14 Insurgents and criminals are not the only sources of danger in Afghanistan. Some of the danger is created by NGOs themselves. Significant changes in the operating attitudes and procedures of NGOs may needlessly increase the danger. European Commission Humanitarian Aid (ECHO), the humanitarian funding and research arm of the European Union, provided a report outlining the pressures faced by NGOs. The following is a summary of that report:
- Despite dangers, NGOs are under pressure to remain within conflicts;
- Donor pressure forces NGOs to operate where they would not have operated in the past;
- The number of NGO operations have increased significantly;
- Past mismanagement of security by an NGO adversely affects the security of others; and
- NGOs may advocate contentious issues that increase resistance to NGOs.30
15 While both insurgents and government forces struggle for dominance, civilians are likely to be the victims of violence and coercion. NGOs attempting to relieve the suffering of these civilians will themselves likely experience the same violence and coercion as the victims. Worse, the insurgents have targeted NGOs because these organizations provide the most significant means for the average Afghan to gain an understanding of the Western world. The insurgents seek to maintain a gap in understanding to ease their manipulation of the population.
16 NGOs face danger when producing intelligence. Activity in excess of a NGO’s mandate may result in unwanted or unwarranted attention. A database is considered a dangerous effort, but the replacement of anecdotal reporting by a systematic collection and analysis method is required if NGO security is to be improved. Even simplistic mapping and analysis may be dangerous in certain environments.31 Maintenance of situational awareness and analysis of geographical patterns, ascertained through plotting events on a topographical map, have been used since the mid-nineteenth century.32 Mapping current events, unexploded ordinances (UXOs), safe havens, and conducting route planning may easily be misinterpreted. For instance, in 2007 there were increased reports of insurgents forcibly entering NGO compounds in search of links to NATO.33 Obviously, NGOs operate successfully using local knowledge that requires limited analysis and can be easily explained using local reference points; however, an international NGO conducting long-term planning requires clear, concise, processed information that reaches beyond the local environment. Despite dangers, NGOs must produce intelligence to meet their mandates, and a safer method would see external actors provide and maintain a security-incident database, continuous analysis, and access-added information resources for NGOs.
17 In summary, because insurgency is a political war, those actors, such as NGOs, that provide stability and enhance government legitimacy are natural insurgent targets. NGOs can provide legitimacy and strengthen the authority of governments like the Islamic Republic of Afghanistan (IRA) by providing the political goods and services that the government may not be able to provide.34 Essentially, insurgent attacks on NGOs undermine the political capital of the Canadian military, reconstruction, and political efforts to bring stability to Afghanistan.
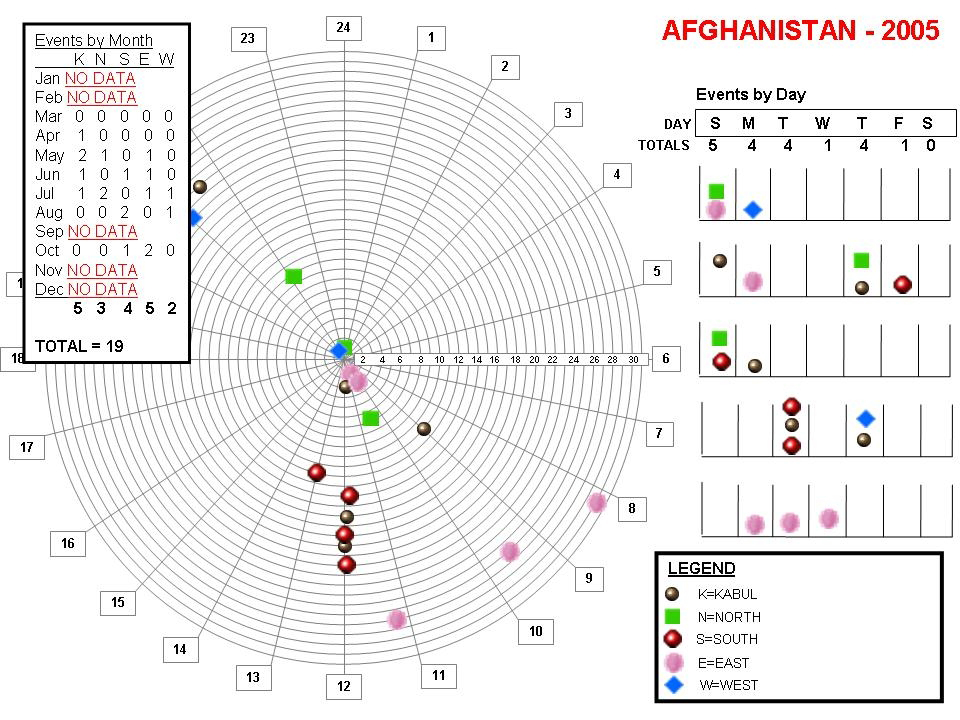
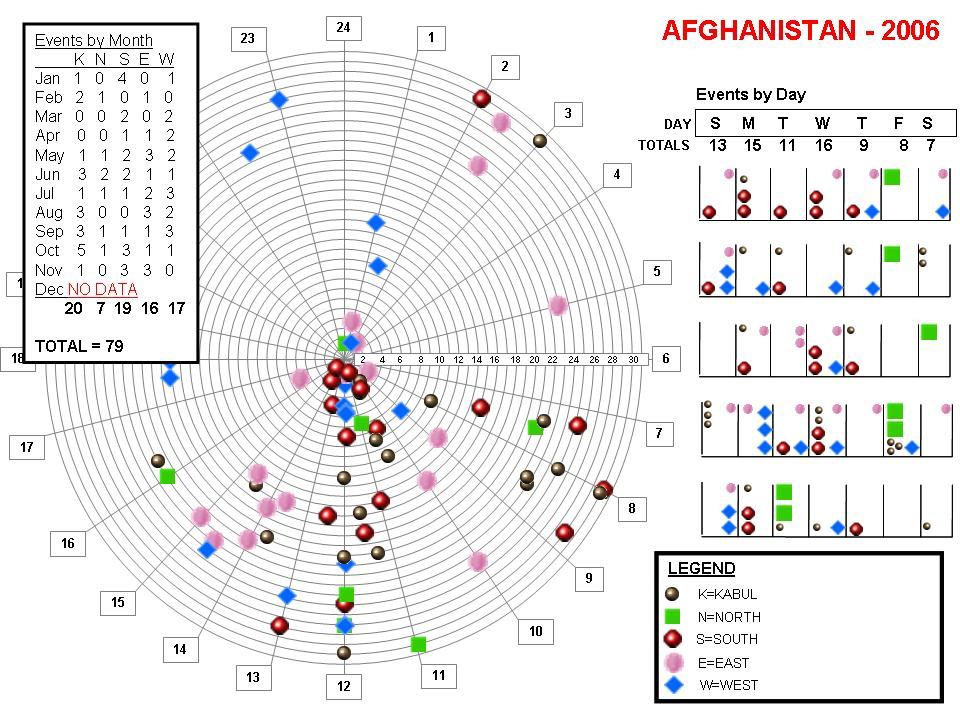
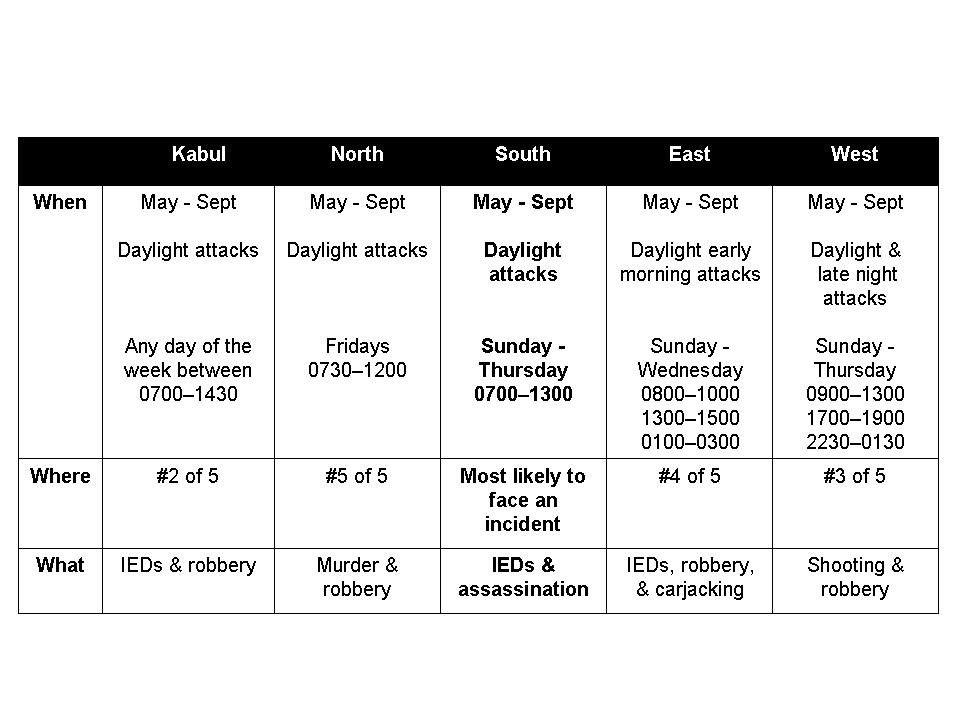
NGOs Have Sufficient Data to Create Intelligence
18 The concept of NGO-driven intelligence is new35 and very few NGOs specialize in intelligence or situational analysis. Nevertheless, a community of NGOs operating in Afghanistan, realizing their shared vulnerability, formed the Afghanistan NGO Safety Organization (ANSO)36 in 2002. Today, the European Union, Swiss Aid, and the Norwegian government fund ANSO. They have five offices (Kabul, Jalalabad, Herat, Kandahar, and Mazar-I-Sharief) with a staff of almost 50 people. However, ANSO does more training of NGOs than it does analysis.37 Their Kabul office acts as the information focal point. It collects security information from the regional security advisors in each of the five operational regions.38 ANSO is the only focal point for NGO security in Afghanistan.
19 ANSO’s products are widely read and freely available on the internet. While the accuracy of incident reporting and the collection of statistics are very good, the reports lack significant analysis or forecasting. The inability to conduct deeper analysis is understandable. Such analysis requires significant investment in personnel to collect and collate data, computing power to conduct multi-method qualitative and quantitative analysis, a well-managed incident database, and time. The quality of ANSO’s products is important because the attempts to reduce risks to NGOs are being outstripped by the evolving insurgency.39
20 NGO-driven intelligence will not be perfect. But NGOs are a vital part of civil society, affecting human security at a local level, with national and international effect. As a result, NGOs need to generate the means to increase their own security. Threats to NGO operations have been growing; therefore, the importance of tailoring security products to a region, town, village, or road is essential. NGOs require a greater understanding of an increasingly complex security environment as a means to ensure their own security. Intelligence provides both an immediate and long-term practical tool to enhance NGO security.
21 Many NGO directors complain about the volume of incident reports they receive and mention that they wish there was more focus on making relevant incidents (those that happened in the same locations as their field offices) more useful. In the field, the volume of information available and the many methods of encountering information are likely to overwhelm managers.40 The number of data sources is only limited by imagination and accessibility to the public and the internet. Managers will likely come to rely on trained personnel to process information for them.41 In fact, ANSO exists because unprocessed information abounds; what is required is greater analysis.42 Clearly, more than enough data exist for NGOs to create their own intelligence. To further illustrate the abundant data and the potential analytical power of academia, the author conducted a case study.
Case Study of NGOs in Afghanistan (2005-2006)
22 Classical intelligence analysis and social science research rarely meet, to the detriment of both intelligence and the social science community. The methods used within this study integrate the two by drawing on their individual strengths. In this case, qualitative methods were emphasized because they are an important means of gathering, analyzing, and interpreting data. Social science methods can add value to traditional intelligence analysis, while traditional intelligence methods preserve context. Both intelligence analysts and social scientists have much to gain through cooperation. What follows is an overview of the research methods used in this case study.
23 As Bob Glasser has asserted, “Grounded theory’s power and usefulness emerge in the realizations which come from doing.”43 Grounded theory, a qualitative approach, was used to complete a portion of this study and is here defined as theory generated from data.44 Adele Clarke’s interpretation of grounded theory in Situational Analysis: Grounded Theory after the Postmodern Turn provides the most suitable method for this study.45 Clarke takes this method and applies the data through a modified version of spatially integrated social science.
24 Grounded theory is used to develop a theory from the data. It is emergent, and since no theoretical models exist that address the study’s interests, it is a valid method. As mentioned, very little literature is written directly on this subject. Glasser stated that grounded theory is the best method to use “. . . where there is virtually no direct literature.”46 Further, the primary variables that address security incidents involving NGOs are not identified, making this study suitable for grounded theory.
25 The second portion of this study was conducted as an intelligence problem using a traditional intelligence method known as pattern wheel or pattern analysis plot sheet.47 The pattern wheel was used to exploit the themes articulated by the grounded theory approach. It visually highlights date and time in rings depicting days of the month and segments depicting hours of the day. Each sheet represents a separate year. The pattern wheel is adaptable and can be used for most time/space/event/group analyses.
26 The combined methods complement each other. Clarke’s grounded theory method provided the mapping to reveal relationships between time, geography, attack types, and targets. Such data is required by the pattern wheel, which further refines and identifies any patterns or associations. This helps to develop theory identifying safer times/locations of operation for NGOs. Understanding the cycles of violence in Afghanistan would provide NGOs the opportunity to avoid threats and increase their freedom of movement without compromising their security.
27 Rarely do intelligence analysts have all of the data or are even aware of all sources of data.48 Gaps in data are likely because trained intelligence personnel do not staff the reporting agency. As a result, it is probable the reporting agency failed to fully report, record, or exploit the data.
28 The findings of the study are summarized in Figure 1 and 2 and Table 1. From the findings, it is clear that attacks on NGOs are seasonal and occur on specific days of the week and times of the day. The data also provided the means of attacks and what the attackers’ objectives may have been, based on the type of security incident. From the data we see that location counts in security, as does proximity to government sites and activity. Importantly, the data indicates that, despite NGO claims of neutrality, the insurgency directly affects NGO insecurity.
29 Based on the data, open-source material can supply sufficient material to provide the basis for pattern analysis allowing for causal, qualitative, and, if desired, quantitative analysis. Understanding the operation environment, which includes weather, belligerents, and terrain, is critical if NGO insecurity in Afghanistan is to be improved.
Providing Security for NGOs
30 NGO-driven intelligence obviously mates two of the three pillars of the Afghanistan Compact, namely security and socio-economic development. It provides the opportunity to share incident data, intelligence products, and to provide NGOs and other development staff the freedom of movement to visit villages and Afghan officials. In general, NGOs do not understand the intelligence that they need.
31 Government agencies and academe need to increase the capacity of NGOs to create their own security. Academics and NGOs share an individualistic nature that may provide academics with a non-intrusive entry point to increase NGO security. Due to organizational culture, military or government agencies may not be as well received as academics. Furthermore, the NGO concept of security is based on acceptance while the military concept of security is based on situational dominance.
32 Both NGOs and the Canadian Forces (CF) are unique subcultures. The organizational culture of NGOs has sometimes created mistrust or misunderstanding among the NGOs, the UN, and various international organizations, including NATO and, by extension, the International Security Assistance Force (ISAF). Understanding the culture, policies, and politics of NGOs adds context to the decisions and practices considered acceptable as well as those that are distasteful. Gaining support and cooperation among NGOs is vital for successful NGO-driven intelligence. Without input, there is little to analyze.
33 A comparison of these two subcultures may assist in understanding why NGOs are so uncomfortable with intelligence. NGO cultures can be characterized as compassionate, people-centered, striving toward economic equality, solving local problems as a means of addressing the root problem, employing locals, looking at long-term objectives, and attempting to fairly distribute resources.49 On the other hand, the military culture can be characterized as mission-driven, timing-driven, direct, clearly ordered, readily identifiable, self-sustaining, and immediate-results orientated.50
34 NGOs are driven to exceed expectations by donors, while the military must complete difficult tasks on order with little warning from their political masters. Military tasks originate from legitimate political masters. These same political masters dictate what constitutes acceptable military practices; conversely, NGOs derive acceptable practices internally and from their donor.
35 Many NGOs prefer to keep an arm’s-length distance from authority as they feel proximity violates their neutrality, a key principle of their acceptance practices.51 Fear of exploitation has led to clear statements regarding information exchanges:
35 Aware of the potential for abuse, misinformation, and loss of their own political agenda, NGOs are wary of intelligence offered by the military or the UN.53
36 Since organizational culture counts, the form that intelligence takes within these NGOs is destined to be different from that of any national intelligence agency. A culture that resists an organized, centralized system poses unique opportunities and challenges in the creation of intelligence. Understanding the importance of organizational culture, an individualistic nature and the need for NGOs to distance themselves from government authority may provide academics with an entry point to enhance the analytic capability of NGO-driven intelligence.
Recommendation
37 Academia has a role to play in the creation of NGO-driven intelligence. Academic methods and studies in many of the social sciences may provide the basis of analysis for NGOs operating in insecure conflict zones. Intelligence is a sensitive subject and can be dangerous to produce. To avoid the danger of producing intelligence, the detailed analytical effort need not reside within Afghanistan. To preserve the context of data and increase the volume, NGOs might consider maintaining and reinforcing NGO intelligence focal points but conducting their analysis from remote locations. Information originating from the field could be forwarded to the focal point and onto another, safer remote location, such as a university or think tank. The focal point for intelligence collection would not have the burden, or danger, associated with the generation of intelligence. It would remove all threats associated with the generation of intelligence but be able to provide up-to-date assessments.
38 Currently, NGO security is based on the occasional field security assessment.54 This practice may impede security because it reduces the opportunity to include daily changes, which can be dynamic and might drastically alter NGO vulnerability. The inability to receive daily inputs, combined with the absence of a single security information database, impairs analysis. Furthermore, a lack of continuity and professional analysis means a clear understanding of the field situation is unlikely. NGOs are usually focused on core tasks such as supplying food, clean water, and medical support. A field-deployed NGO does not have the time, computing resources, training, or opportunity to generate intelligence even when assigned that task. The process of creating intelligence is specialist work that is complex and time- and resource-consuming, and there are dangers associated with the generation of intelligence that NGOs donors may not be willing to endure.
39 Leveraging and remotely exploiting data provided by NGOs would allow analysts and academics the freedom to provide high-quality causal, qualitative, and quantitative research products.55 Combinations of models and methods could result in effective intelligence. Regardless of the analytical tools used — whether causal mechanisms or qualitative or quantitative research methods — IT support is required. The opportunity to exploit data hidden within NGOs requires advanced training and computing power, neither of which is easily found in conflict zones, making remote data exploitation even more attractive.
40 Remote location analysis would offer several advantages, including an opportunity to provide objective analysis of power dynamics, regional and local analysis, and conflict monitoring. Distance removes political pressure. In Afghanistan, there are several sources of political pressure, including, but not restricted to, the IRA, Taliban, warlords, organized crime, and personal interest. Distance encourages the analyst to adopt a dispassionate approach resulting in bias-free assessment. NGO-driven intelligence products could avoid intelligence tailored to suit a preferred policy.56
41 Remote analysis may not be that difficult to establish once agreement among NGOs has been reached. A researcher with appropriate field experience, a research grant from the Social Sciences and Humanities Research Council, a reduced teaching load, and a small team of graduate students would provide a senior researcher all that is necessary to begin to increase the security of NGOs. Similar work has been undertaken at other universities that research human security.
42 Remote analysis is not perfect. The success of this concept is dependant on sustained agency buy-in, the development of a good governance structure, and the availability of accessible and effective technological solutions.
CONCLUSION
43 NGO-driven intelligence has many advantages, especially in Afghanistan, where it offers security and socio-economic development. It also enables NGOs to share incident data and provides them and other development staff with freedom of movement to operate among Afghans. The concept brings into play funding, resources, capabilities, and staff that have not been leveraged for NGO security to this point.
44 NGO insecurity can be mitigated through increased analysis of open-source data. Little theory exists regarding NGO insecurity; however, strands of evidence, based on basic pattern analyses conducted in this study, indicate that NGO-driven intelligence could significantly contribute to the safety of NGOs in Afghanistan. Unstructured data from NGO security-incident reports provided sufficient information to create basic intelligence. The study, without fully exploiting the data, clearly indicates that even limited open-source information could provide the means to create NGO-driven intelligence and assist NGOs in avoiding potential security incidents within Afghanistan.
45 Theory must be tentative in nature, making a grounded theory approach effective in this case. Grounded theory is emergent and is intended to provide an understanding of a researched situation. Few would disagree that insecurity in Afghanistan continues to evolve and requires constant study because insurgent tactics, techniques, and procedures (TTPs)57 also evolve; although ad hoc NGO mitigation practices are effective today, they may not be tomorrow. In the end, NGO mitigation practices, such as acceptance practices, will likely need to evolve to meet the challenges of NGO insecurity in Afghanistan.
46 NGOs remain vulnerable to criminality and insurgent activity and, as the literature illustrates, are increasingly identified with the government. Security incidents are increasingly violent, with improvised explosive devices (IEDs) becoming more common. Ultimately, humanitarian work is about action, not necessarily reason; however, actions without consideration for the operating environment will likely result in the undoing of all good works.
47 Intelligence is not the key to success in NGO operations; many successful NGO efforts have occurred without the benefit of intelligence. However, in increasingly unrestrained conflicts, NGO-driven intelligence, assisted by remote analysis provided by academia, may prevent the deaths of NGO personnel, and the loss of equipment and valuable aid.